🚫 What is the Quantum Threat & Why Do We Need Quantum-Safe Architectures?
Quantum computing will shatter the cryptographic foundations of today’s digital systems. Algorithms like RSA and ECC, which protect most data lakes, VPNs, TLS communications, and disk encryptions, are vulnerable to Shor’s algorithm on a fault-tolerant quantum computer.
Impact: Any data encrypted today could be harvested and decrypted in the future — a strategy known as “harvest now, decrypt later.”
Data lakes are prime targets due to:
Long data retention periods
High-value historical and personal data
Legacy encryption algorithms
The need for quantum-safe data architecture is no longer optional. It’s essential for forward-thinking CTOs, CDOs, CISOs, and cloud data architects responsible for safeguarding data estates.
🌎 Global Readiness: Who’s Taking Action?
Governments and security bodies are actively responding to the quantum threat:
✅ USA: NIST PQC project began in 2016, selecting new cryptographic standards (e.g., Kyber, Dilithium)
✅ White House (NSM-10): Mandates all federal systems to migrate to quantum-safe algorithms
✅ EU & ENISA: Guiding crypto-agility and PQC adoption
✅ UK (NCSC): Advises early quantum threat preparation
✅ China: Launched the first quantum satellite (Micius) and invests heavily in quantum secure networks
✅ Singapore: National Quantum Strategy launched under QEP with GovTech awareness
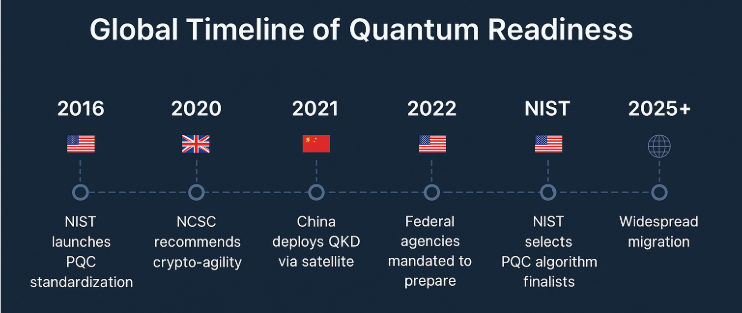
Fact: NIST PQC standards are expected to finalize by 2024–25. The migration window is now open.
⚠️ Why Are Traditional Data Lakes at Risk?
1. Data at Rest Encrypted with RSA/ECC: Encrypted S3 buckets or Parquet archives using RSA/ECC can be broken by quantum computers in the near future.
2. Harvest Now, Decrypt Later: Threat actors may steal encrypted data now and store it to decrypt later, once quantum decryption becomes practical.
3. TLS Encryption Using RSA: TLS handshakes between data ingestion tools, BI systems, and warehouse layers may use RSA-based encryption, which quantum can break.
4. KMS and Key Wrapping Schemes: Key management services (KMS) that rely on RSA/ECC wrapping must migrate to post-quantum-safe schemes for long-term protection.
5. Long-Term Confidentiality Loss: Data stored with RSA-2048 can be cracked in minutes by quantum computers.
6. Unprotected Backups: Cold or archived data may remain vulnerable for years.
7. Data-in-Transit Risks: Internal TLS tunnels and APIs may be quantum-breakable.
8. Third-Party Integrations: Vendors may use legacy crypto unknowingly.
9. Poor Crypto Inventory: Lack of visibility into where and how encryption is used.
✅ Assessment Checklist
Inventory asymmetric encryption usage (RSA, ECC)
Identify data with 5+ year retention (high risk)
Locate legacy backups and cold storage archives
Document TLS certificates and key exchange methods
Review third-party tools for outdated crypto
✨ What is Post-Quantum Cryptography (PQC)?
PQC refers to new cryptographic algorithms designed to resist both classical and quantum attacks.
NIST has recommended the following families:
CRYSTALS-Kyber: Public key encryption/key encapsulation
CRYSTALS-Dilithium: Digital signatures
These are software-based and do not require quantum computers to implement. They are classical algorithms resistant to quantum attacks.
☁️ Can It Be Integrated into Traditional Cloud Data Lakes?
Yes. PQC can be integrated using client-side or envelope encryption within existing cloud-native architectures. It does not require high-performance hardware upgrades.
AWS
Use custom key wrapping with Kyber (via Lambda + AWS KMS external)
Store data keys wrapped in PQC-resistant formats
Azure
Azure Key Vault roadmap supports crypto-agility
Implement client-side PQC via SDKs or Tink
GCP
Use Google Tink for hybrid or PQC key wrapping
PQC handshake in mutual TLS for internal workloads
Hadoop/Spark
Integrate PQC encryption in HDFS or during Spark ingestion jobs
Use external vaults (e.g., HashiCorp Vault + PQC plug-in)
PQC integration is a software-level upgrade — not hardware-intensive. Ideal for hybrid and cloud-native data lakes.
✅ Quantum-Readiness Checklist for Data Lake Architects
| Domain | Action Required |
|---|---|
| Encryption | Inventory all symmetric/asymmetric algorithms in use |
| Backups | Plan to re-encrypt cold storage with PQC |
| Key Management | Adopt crypto-agile KMS solutions with PQC roadmap |
| Third-Party Tools | Require vendors to disclose crypto standards |
| TLS & API | Test hybrid TLS (classical + PQC) for internal APIs |
| Compliance | Align with NIST PQC and national guidance (e.g., NSM-10) |
⏳ How to Start Today (Quantum-Safe Actions)
-
Crypto Inventory: Map every encryption algorithm across storage, compute, and communication layers
-
Adopt Crypto-Agility: Build systems where algorithms can be swapped/upgraded with minimal re-architecture
-
Implement Hybrid Encryption: Use Kyber + AES or similar hybrid wrappers
-
Test PQC Libraries: e.g., Open Quantum Safe, Google Tink, AWS LibCrypto
-
Educate Teams: Train architects and security teams in PQC algorithms and tools
Quantum-safe readiness is not a switch — it’s a phased journey. Start now, migrate progressively.
🔒 Your Data Lake Deserves Quantum-Grade Protection
“The adversary is preparing. So must we.”
Quantum computing will render today’s encryption obsolete. But data lakes hold the crown jewels — decades of proprietary, regulatory, and PII data. Waiting is not an option.
A quantum-safe data architecture is within reach. By inventorying, encrypting, wrapping, and testing PQC today, architects can future-proof their platforms and outpace threats.
Act now. Crypto-agility and PQC are the foundation of tomorrow’s secure data platform.
